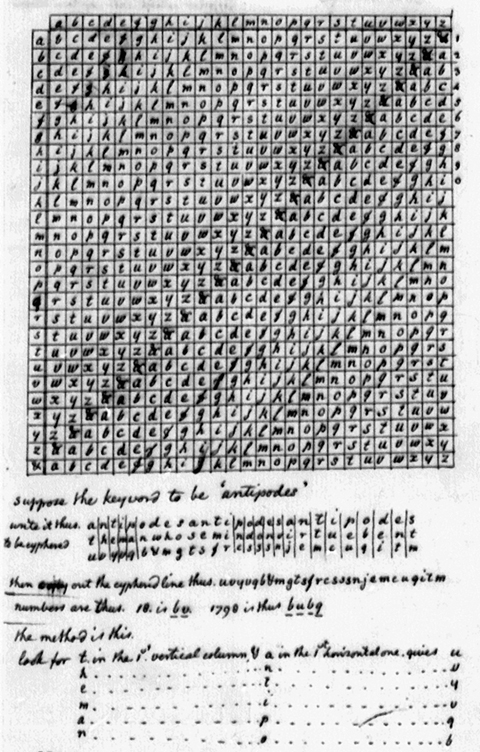
Sometime in 1803 Thomas Jefferson presented Meriwether Lewis with a cipher based on a square table or tableau such as that published in 1516 by Johannes Trithemius, a Benedictine abbot in Germany, and which had found common usage during the eighteenth century. It is used to create a substitution cipher, in which any letter of the alphabet is made to stand for another letter. The top row and the extreme left-hand column are the basic coordinates. A keyword is used for simplicity and speed in encoding and decoding.
To encode numbers, write the them beneath the letters of the password, in this instance “antipodes.” Reading from the figure 1 across to the a in the top row, then down that column to the first a in the left column will produce an encoding of b. To encode the number 8 in 18, follow the number 8 across to the n column, which intersects with the 8 line at the letter v. The number 1798 is represented by the password letters as a, n, t, and i. Those four numbers and their corresponding letters intersect at the code letters b, u, b, and q, which is the ciphered form of 1789.[1]We are indebted to Sharon Touton of Pasadena, California, for calling attention to our errors in the original version of this page, and for clarifying the encoding of numbers with Jefferson’s … Continue reading
In the official orders he issued in April 1803, Jefferson urged Lewis to keep him informed “at seasonable intervals” concerning the progress of the expedition, “putting into cypher whatever might do injury if betrayed.”[2]Donald Jackson, Letters of the Lewis and Clark Expedition with Related Documents (2nd ed., 2 vols., Urbana: University of Illinois Press, 1987), 1:65. Lewis himself never mentioned the cipher in any correspondence, nor in his journals, and there is no other evidence that he ever resorted to it. That Jefferson, however, initially took the idea seriously is suggested by the fact that he devised two slightly different ciphers with Lewis’s journey in mind.
Origins
Cryptology—from the Greek words kryptos, “hidden,” and logos, “word”—began as the science of communicating critical information, usually of a political or military nature, in a secret language known only to the sender and the legitimate receiver. The source information is called the plaintext. The secret formula for encrypting the plaintext is called the key. The result of the encryption is called the cipher (often spelled cypher) or ciphertext. The process of applying a key to a cipher in order to decode it is known as decryption. Ciphers systematically substitute letters or numbers for the letters in a message; codes consist of symbols, words, or groups thereof, which stand for other words, parts of words, or ideas. For example, Lewis used a set of symbols to encode his evaluations of Army officers for Jefferson (see Lewis’s Report on Army Officers). In general, codes and ciphers were not applied to entire letters or other documents, but only to names, actions, and judgments.
The origins of cryptology lie deep in the history of written languages, when Arabic scholars began systematically studying the subject. Its use became widespread beginning in the sixteenth century, when intercontinental exploration resulted in the building of farflung empires. By the eighteenth century most European countries, including France, England, Spain, and the great city-states of Venice and Florence in Italy, had developed a wide variety of intricate and effective cryptographic systems, including the bureaucratic structures not only to maintain secure communications but also to pursue interception and code-breaking.
Early American Uses
The founders and leaders of the early American republic were dedicated to the “rule of reason” and to honesty and openness in domestic and foreign diplomacy. John Adams, resisted the very idea of secrecy. However, during the years when Jefferson was the U.S. minister to France (1784-1789), and Adams was minister to England, ciphers were essential because European postmasters routinely opened and read all foreign correspondence. At the apporoach of the Revolutionary War came the realization of a need for an alliance with France, which involved confidential communications with the government of Louis XVI, as well as the gathering and transmittal of information concerning British resources and strategies. To meet those needs, on 29 November 1775, the Second Continental Congress established a Committee of Secret Correspondence—soon renamed the Committee of Foreign Affairs. Among other things, it was responsible for employing secret agents abroad, conducting covert operations, authorizing the opening of private mail,[3]The Bill of Rights—the first ten Amendments to the Constitution—including the right to freedom of speech (the First Amendment) was ratified in 1791. This guarantee was seldom invoked during the … Continue reading and designing codes and ciphers. One of the more prominent members of the Committee was Benjamin Franklin; one of the most influential French agents was Pierre-Augustin Caron de Beaumarchais.[4]“Intelligence in the War of Independence,” http://www.cia.gov/cia/publications/warindep/frames.html. Accessed 18 February 2006. Beaumarchais is best remembered today as the author of two … Continue reading
The United States was obliged to re-enter the arena of coded communication during the murky XYZ Affair of 1797-98, which briefly darkened Franco-American relations. Without a single official cryptographer, the country would have been at a considerable disadvantage in the field of secret correspondence had it not been for innovators such as James Lovell (1737-1814), who developed a cipher system in the 1770s that was used during the Revolution Era of 1775-1789. So-called book codes were also developed. These employed lexicons such as John Entick’s New Spelling Dictionary of the English Language[5]Published in London in 1764, Entick’s Dictionary was widely used throughout the U.S. Noah Webster, who called it “the best compilation of the kind,” used it as the model for his … Continue reading as sources, with codes referencing words by encrypted page numbers and columns.
The U.S. postal service had been established under Benjamin Franklin’s supervision in 1775. Most mail was carried on designated post roads by members of a small company of post riders. Otherwise, letters and packages might be carried as a favor by anyone who happened to be traveling toward a correspondent’s destination. In either case, carriers often felt free to break the wax seals and read the missives entrusted to them. At that time there was no more of a sense of privacy or privilege than exists today in the transmission of email.
Jefferson’s Impetus
Meanwhile, the power-struggle between the Federalists, who sought reconciliation with Great Britain, and the Jeffersonian Republicans, who were devoted to France and French revolutionary values, with its related international implications, soon made secrecy essential on both sides.
It was Thomas Jefferson who gave cryptography in America its greatest impetus. Beginning with his tenure as Secretary of State in 1790, and especially upon his election to the presidency in 1801, he became a participant in the political life of the Western Hemisphere at large, and the encoding of dispatches between the government and its representatives in various European capitals became imperative. The intrigues involving the pirates of the North African Barbary Coast, as well as the conspiracy between Aaron Burr and James Wilkinson aimed toward carving out a new territory in the Southwest, also involved coded communications. One of Jefferson’s most remarkable innovations was the wheel cipher.
During Jefferson’s administration the most commonly used code was a “nomenclator” consisting of 1700 consecutively numbered but randomly arranged words and syllables. Numbers 150 through 160, for example, happen to begin with the letter d—150 dist, 151 dispose, 152 dispatch, 153 disp, 154 dish, 155 disc, 156 disaffect, 157 dis, 158 dir, 159 din, 160 dim—but there is another sequence of d-words between 1301 and 1350, which are not otherwise in alphabetical order. A message, or part of a message, encoded in this 1700-element nomenclator would consist of a series of apparently random numbers separated by periods. Of course, the addressee had to have a copy of the nomenclator in order to decode the message. A typical example of Jefferson’s use of encryption, from a letter he wrote to James Monroe in Paris on 6 September 1795, reads as follows, with the words originally in code shown in italics.
In political matters there is always something new. Yet at such a distance and with such uncertain conveyances it is best to say little of them. It may be necessary however to observe to you that in all countries where parties are strongly marked, as the monocrats and republicans here, there will always be desertions from one side to the other, and to caution you therefore in your correspondences with Dawson who is now closely connected in speculations as we are told with Harry Lee with Steel become a consummate tory, and even Innes who has changed backwards and forwards two or three times lately.[6]Papers of Thomas Jefferson (31 vols, Princeton, New Jersey: Princeton University Press, 1950-1997), 28:449. The names in italics, originally written in code, were deciphered by the editors of the … Continue reading
Another Lewis Cipher
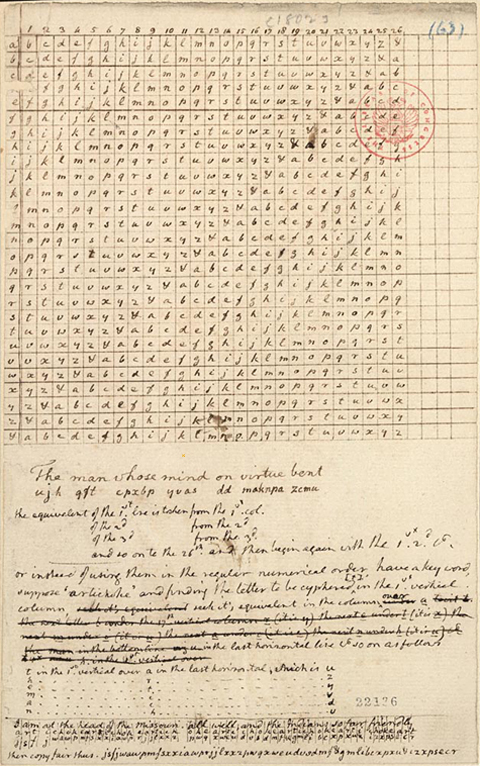
This cipher, which Jefferson may have drafted earlier than the preceding one, establishes coordinates using the left column and bottom row of the matrix.[7]Jackson, 1:10. Similarly, it uses all 26 letters of the alphabet, plus the ampersand (&) symbol.
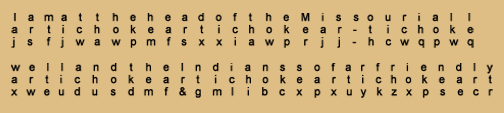
The partially legible writing at the bottom of the page shows the encryption of Jefferson’s sample plaintext, which reads: “I am at the head of the Missouri. All well and the Indians so far friendly.”
Jefferson then illustrates the encoding of the plaintext. The letters of the keyword artichoke are distributed, in order, beneath the letters of the plaintext. Using the procedure applied to the other sample plaintext, “The man whose mind . . .” etc., Find the first letter of artichoke in the column at extreme left. Find the first letter of the plaintext in the bottom row of characters. The letter at which the two coordinates intersect, j, is the first letter of the encryption. Find the second letter of the key word in the left column. Find the second letter of the plaintext in the bottom row. The letter at which the two coordinates intersect is s, which is the second letter in the encryption.
Jefferson concluded: “then copy fair thus”:
jsfjwawpmfsxxiawprjjhcwqpwqxweudusdmf&gmlibcxpxuykzxpsecr
The message is decoded by the recipient in the following way: Write the letters of the keyword, artichoke, above the successive letters in the encoded message. Locate the keyword letter a (the first letter in artichoke) in the bottom row; trace that column upward until arriving at the code letter j. Follow that row to the left to locate the plaintext letter I in the first column. Next, find the keyword letter r in the bottom row; trace that column up to the code letter s; follow that row to the first column at left, which yields the plaintext letter a. And so on.
Jefferson’s Wheel Cipher
The most advanced cipher of its time, according to historian David Kahn, was Thomas Jefferson’s wheel cipher.[8]David Kahn, The Codebreakers: The Story of Secret Writing (New York: Macmillan, 1967), 195. Jefferson created it in the early 1790s while he was President George Washington’s secretary of state. Sometime prior to the end of March, 1802, Jefferson described his device, in part, as follows:
Turn a cylinder of white wood of about 2. Inches diameter & 6. or 8. I. long. bore through it’s center a hole sufficient to recieve an iron spindle or axis of 1/8 or 1/4 I. diam. divide the periphery into 26. equal parts (for the 26. letters of the alphabet) and, with a sharp point, draw parallel lines through all the points of division, from one end to the other of the cylinder, & trace those lines with ink to make them plain. then cut the cylinder crosswise into pieces of about 1/6 of an inch thick. they will resemble back-gammon men with plane sides. number each of them, as they are cut off, on one side, that they may be arrangeable in any order you please. on the periphery of each, and between the black lines, put all the letters of the alphabet, not in their established order, but jumbled, & without order, so that no two shall be alike. now string them in their numerical order on an iron axis, one end of which has a head, and the other a nut and screw; the use of which is to hold them firm in any given position when you chuse it. they are now ready for use, your correspondent having a similar cylinder, similarly arranged. . . . numbers [are] represented by letters with dots over them.[9]Ralph E. Weber, United States Diplomatic Codes and Ciphers, 1775-1938 (Chicago: Precedent Publishing Inc., 1979), 170-72.
To cipher a phrase such as “your favor of the 22d is received,” the letter y is located on the wheel at the left end of the instrument; the next wheel is turned until the letter o is adjacent to the y; the third wheel is turned until u is next to the o; and so on, until all words in the message are spelled out in up to 26 letters, with no spaces between them. Each of the remaining rows of letters on the cylinder represents a different encryption of the message, or plaintext. To transmit the cipher, the sender copies the sequence of letters in one row in a letter and mails it off. The recipient arranges the letters on any row of his cylinder into the sequence received, then rotates the whole cylinder until a meaningful series of words can be recognized. For messages of more than 26 letters, the same procedure is followed as many times as necessary. By merely changing the order of the wheels in the cylinder, Jefferson pointed out, “an immense variety of different cyphers may be produced for different correspondents.”
The main drawback to Jefferson’s wheel cipher was that replicas had to be distributed in advance to all potential correspondents, which included several in the capitals of Europe, a process that could take months. Jefferson soon turned to written cipher systems that were more convenient. In 1890, however, a French cryptologist devised a similar device. Then the U.S. Army introduced an electrical version prior to World War I, and used it continually until the early 1940s. Since the early 1970s, microprocessors have been used to facilitate encryptions that penetrate the daily lives of most people throughout the world, either directly or indirectly.
Other Sources
Ralph E. Weber. United States Diplomatic Codes and Ciphers, 1775-1938. Chicago: Precedent Publishing Inc., 1979. Especially Chapter 6, “Experimentation and Crises, 1801-1815.”
Arlen J. Large, “Lewis and Clark Under Cover,” We Proceeded On, Vol. 15, No. 3 (August 1989), 12-22.
Ann M. Lucas, “Thomas Jefferson’s Wheel Cipher,” September 1995; with revisions by Chad Wollerton, December 2003. Thomas Jefferson Foundation, Inc., http://www.monticello.org/reports/interests/wheel_cipher.html/ (accessed 2 February 2005).
Notes
| ↑1 | We are indebted to Sharon Touton of Pasadena, California, for calling attention to our errors in the original version of this page, and for clarifying the encoding of numbers with Jefferson’s cipher. |
|---|---|
| ↑2 | Donald Jackson, Letters of the Lewis and Clark Expedition with Related Documents (2nd ed., 2 vols., Urbana: University of Illinois Press, 1987), 1:65. |
| ↑3 | The Bill of Rights—the first ten Amendments to the Constitution—including the right to freedom of speech (the First Amendment) was ratified in 1791. This guarantee was seldom invoked during the 19th century, and became a major sociopolitical issue only after World War I. |
| ↑4 | “Intelligence in the War of Independence,” http://www.cia.gov/cia/publications/warindep/frames.html. Accessed 18 February 2006. Beaumarchais is best remembered today as the author of two plays, The Barber of Seville and The Marriage of Figaro, which were transformed into two of the most popular and enduring operas, composed by Giacomo Rossini and Wolfgang Amadeus Mozart, respectively. |
| ↑5 | Published in London in 1764, Entick’s Dictionary was widely used throughout the U.S. Noah Webster, who called it “the best compilation of the kind,” used it as the model for his Compendious Dictionary of the American Language (1806). Harlow Giles Unger, The Life and Times of Noah Webster, an American Patriot (New York: John Wiley and Sons, 1998), 251. |
| ↑6 | Papers of Thomas Jefferson (31 vols, Princeton, New Jersey: Princeton University Press, 1950-1997), 28:449. The names in italics, originally written in code, were deciphered by the editors of the Papers using “Code No. 9” |
| ↑7 | Jackson, 1:10. |
| ↑8 | David Kahn, The Codebreakers: The Story of Secret Writing (New York: Macmillan, 1967), 195. |
| ↑9 | Ralph E. Weber, United States Diplomatic Codes and Ciphers, 1775-1938 (Chicago: Precedent Publishing Inc., 1979), 170-72. |
Experience the Lewis and Clark Trail
The Lewis and Clark Trail Experience—our sister site at lewisandclark.travel—connects the world to people and places on the Lewis and Clark Trail.
Discover More
- The Lewis and Clark Expedition: Day by Day by Gary E. Moulton (University of Nebraska Press, 2018). The story in prose, 14 May 1804–23 September 1806.
- The Lewis and Clark Journals: An American Epic of Discovery (abridged) by Gary E. Moulton (University of Nebraska Press, 2003). Selected journal excerpts, 14 May 1804–23 September 1806.
- The Lewis and Clark Journals. by Gary E. Moulton (University of Nebraska Press, 1983–2001). The complete story in 13 volumes.